Design active directory forest trust
Most of the enterprise organization often deploys multiple forests. Although these forests are usually designed for separate divisions of their organization, sometimes it needs integration between these separated forests. The most common way of allowing users in one forest to access the resources located in another is to configure an interforest trust so that any user in any domain in the trusted forest can access any resource in any domain in the trusting forest. An alternative is an external trust that exists between specific domains in different forests rather than in any domain in each forest.
At the time of forest trust designing we need to consider the number of forests to be trusted, direction of trust, user selective authentication and necessary SID filtering.
When we design a trust direction, we must ensure that only the minimum requirement grant to meet the business requirement. We can also limit trust by using selective authentication, which restricts the number of users in the trusted forest who are able to access shared resources in the trusting forest. SID filtering also can use for prevent users to use trust resources.
Implementing active directory forest trust
Before we implement active directory forest trust we need to ensure that domain name system (DNS) is properly set up.
If there is a root DNS server that can be made the root DNS server for both of the forest DNS namespaces, make it the root server by ensuring that the root zone contains delegations for each of the DNS namespaces. Also, update the root hints of all DNS servers with the new root DNS server.
If there is no shared root DNS server and the root DNS servers for each forest DNS namespace are running a member of the Windows Server 2003 family, configure DNS conditional forwarders in each DNS namespace to route queries for names in the other namespace.
If there is no shared root DNS server, and the root DNS servers for each forest DNS namespace are not running a member of the Windows Server 2003 family, configure DNS secondary zones in each DNS namespace to route queries for names in the other namespace.
Also set the forest functional level either “Windows server 2003” or more then “Windows server 2003”.
Step 1
Here our 1st forest is test.com. We configure two way trusts with this domain and abc.com. Now we configure in 1st forest.
Click Start, click Administrative tools.
Then click Active Directory Domain and Trust.
In the console tree right click the domain (i.e. test.com) and click on Properties.
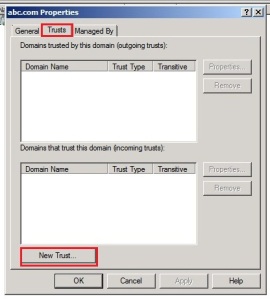
From properties dialog box click on Trust tab and click on New trust.
Then new trust wizard run and click on Next button.
On the trust name dialog box write FQDN of the domain we need to trust (i.e. vms102.abc.com), click on Next button.
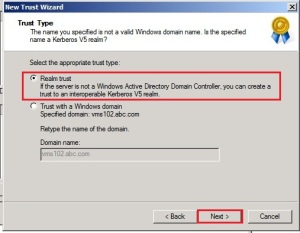
In trust type dialog box click on Realm trust radio button and click on Next button.
From transivity of trust dialog box click on Transitive radio button and click on Next button.
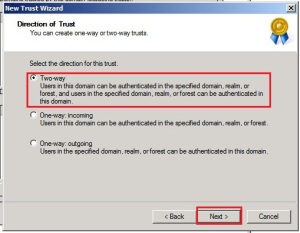
In direction of trust dialog box click on Two-way radio button and click on Next button.
From trust password dialog box write password on Password and confirm Password text box then click on Next button.
In trust selection dialog box click on Next button.
Now click on Finish button.
From one side trust implementation complete.
See there is the name of root domain that tasted, click on Ok button.
Step 2
Trust Configure in second forest.
Click Start, click Administrative tools.
Then click Active Directory Domain and Trust.
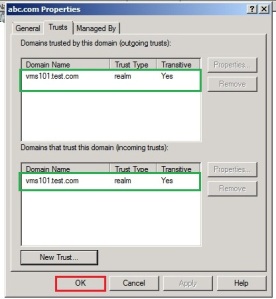
In the console tree right click the domain (i.e. abc.com) and click on Properties.
From properties dialog box click on Trust tab and click on New trust.
Then new trust wizard run and click on Next button.
On the trust name dialog box write FQDN of the domain we need to trust (i.e. vms101.test.com), click on Next button.
From transivity of trust dialog box click on Transitive radio button and click on Next button.
In direction of trust dialog box click on Two-way radio button and click on Next button.
From trust password dialog box write password on Password and confirm Password text box then click on Next button.
In trust selection dialog box click on Next button.
Now click on Finish button.
Here trust complete from other side.
See there is the name of root domain that tasted, click on Ok button.